wiesiek.euSplunk combine fieldsuk granny chatuk granny datinguk granny dido fuckuk granny fuckuk granny fuck pornhubuk granny pussyuk granny pussy tumblruk granny sexuk granny sex chatuk granny sex contact |
wiesiek.eu
braun detachable led flood light
wm rogers overlaid is patterns
fruit platter wegmans
does csl plasma hire felons
2014 ram 1500 fuse diagram
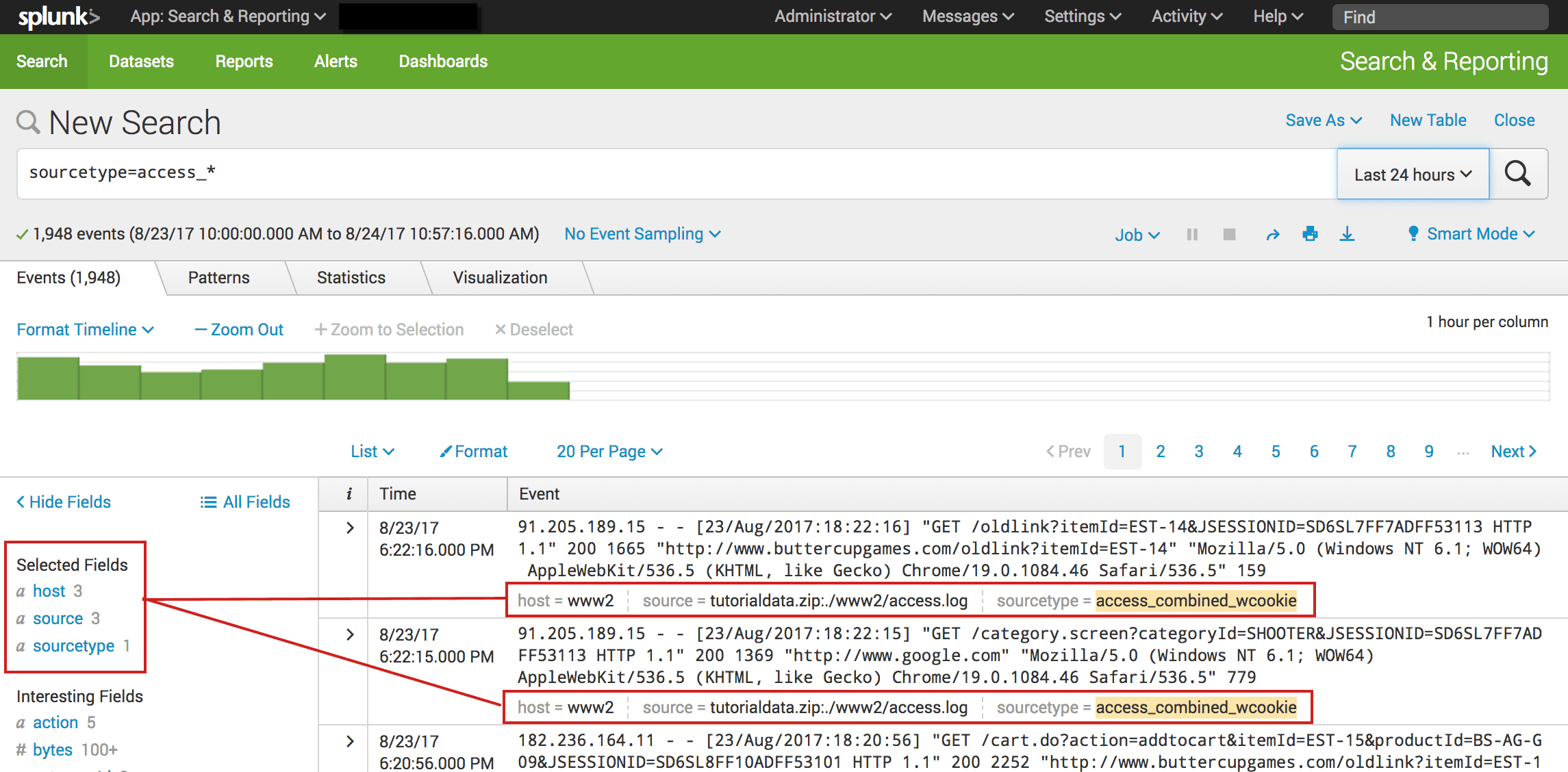
Splunk is a powerful platform that allows organizations to collect, analyze, and visualize their machine-generated data. With its versatile capabilities, Splunk enables users to gain valuable insights and make informed decisions based on their data. One of the key features of Splunk is its ability to combine fields, which plays a crucial role in data analysis and interpretation.
Combining fields in Splunk involves merging or concatenating multiple fields to create a new field. This process allows users to manipulate and transform their data, enabling them to derive meaningful insights. By combining fields, users can create new dimensions and metrics that enhance their data analysis capabilities.
There are several scenarios where combining fields in Splunk proves to be beneficial. For instance, in log analysis, combining fields can help in correlating different log events and identifying patterns. It can also enable users to create more meaningful visualizations by grouping data based on combined fields. Additionally, combining fields is useful when creating custom reports, dashboards, and alerts in Splunk.
To combine fields in Splunk, users can leverage the powerful search processing language (SPL) provided by the platform. SPL offers a wide range of functions and operators that enable users to manipulate their data effectively. Some commonly used SPL functions for combining fields include "eval", "concat", "mvcombine", and "rex".
The "eval" function is used to create new fields by performing calculations or transformations on existing fields. It allows users to combine fields using arithmetic operators, string functions, or logical operators. For example, to combine the "firstname" and "lastname" fields into a new field called "fullname", the following SPL command can be used: `eval fullname = firstname . " " . lastname`.
The "concat" function is specifically designed for combining fields. It concatenates multiple fields into a single field, separated by a specified delimiter. This function is particularly useful when dealing with fields that contain multiple values, such as arrays or multivalue fields. For example, to combine the values of the "country" field and the "city" field into a new field called "location", the following SPL command can be used: `eval location = concat(country, ",", city)`.
The "mvcombine" function is used to combine multivalue fields into a single value. It concatenates the values of the multivalue field, separated by a specified delimiter. This function is commonly used when dealing with fields that contain multiple values, such as IP addresses or user IDs. For example, to combine the values of the "ip" field into a new field called "combined_ip", the following SPL command can be used: `eval combined_ip = mvcombine(ip, ",")`.
The "rex" function is used to extract and combine fields using regular expressions. It enables users to extract specific patterns from fields and combine them into a new field. This function is particularly useful when dealing with unstructured or semi-structured data. For example, to extract the date and time from a log event and combine them into a new field called "timestamp", the following SPL command can be used: `rex field=_raw "(?P uk granny chat. 1 Solution Solution brettgladys Explorer 10-19-2010 06:10 PM Well.a typo did it. eval fullName=applicationName. "-" .servletName Turns out that not putting the right name of a field causes the entire operation to return nada splunk combine fields. View solution in original post 20 Karma Reply All forum topics Previous Topic Next Topic chris Motivator
uk granny dating. 1 Solution Solution mparks11 Path Finder 03-02-2015 02:20 PM | fillnull value="" name_1 name_2 name_3 | eval combined_user=name_1.name_2.name_3 This will fill a null value for any of name_1, name_2 or name_3, but since you dont want to actually fill the null value with an actual value, just use double quotes.. Solved: How to combine multiple fields? - Splunk Community. How to combine multiple field values to create single field name in eval statement. Get Updates on the Splunk Community! New Enhancements with Splunk Enterprise 9.1uk granny dido fuck. strcat - Splunk Documentation. <source-fields> Syntax: (<field> | <quoted-str>) splunk combine fieldsuk granny fuck. Description: Specify the field names and literal string values that you want to concatenate splunk combine fieldsuk granny fuck pornhub. Literal values must be enclosed in quotation marks splunk combine fieldsuk granny pussy. quoted-str Syntax: "<string>" Description: Quoted string literals. Examples: "/" or ":" splunk combine fields. How to merge two fields values into a single field? - Splunk Community. 1 Solution Solution xpac SplunkTrust 05-06-2018 10:54 PM Hey, This looks like the perfect use case for coalesce (): | eval Method=coalesce (Method, Action) Read up on its details here: ocs.splunk.com/Documentation/Splunk/7.1./SearchReference/ConditionalFunctions View solution in original post 3 Karma Reply All forum topics Previous Topic. Merging common values from separate fields - Splunk Lantern splunk combine fieldsuk granny pussy tumblr. You want to create a third field that combines the common values in the existing fields. Solution You can accomplish this using a number of multivalue evaluation functions. The following search uses the two values above and returns the following value: 1237.. How to combine two fields to one field - Splunk Community. Solved: How to combine two fields to one field - Splunk Community Solved! Jump to solution How to combine two fields to one field prashanthberam Explorer 11-14-2016 12:33 PM I WANT TO COMBINE THOSE TIMESTAMP INTO ONE COLUMN HOW CAN I DO THAT BUT I DONT WANT USE THE TRANSACTION COMMAND HELP ME GUYS THE SAMPLE TABLE ID TIMESTAMP1 TIMESTAMP2. join - Splunk Documentation. join Description. You can use the join command to combine the results of a main search (left-side dataset) with the results of either another dataset or a subsearch (right-side dataset)
uk granny sex. Splunk: combine fields from multiple lines Ask Question Asked 2 years, 10 months ago Modified 2 years, 10 months ago Viewed 2k times 1 Context Say I have logs structured this way. Evaluate and manipulate fields with multiple values - Splunk. If you are using Splunk Enterprise, you can configure multivalue fields in the fields.conf file to specify how Splunk software detects more than one field value in a single extracted field value. Edit the fields.conf in $SPLUNK_HOME/etc/system/local/, or your own custom application directory in $SPLUNK_HOME/etc/apps/.. Re: Merge the field value and its count into one field. How to merge the field value and its count into one field? man03359. Explorer 06-02-2023 08:01 AM. I am relatively new to Splunk and I am trying to create a field that contains the field value and its count into one merged field, The pattern looks like this: 31/05 .. Combining commands - Splunk Documentation. Combining commands. You can combine commands. The pipe ( | ) character is used to separate the syntax of one command from the next command. The following example reads from the main dataset and then pipes that data to the eval command. You use the eval command to calculate an expression. The results of that expression are placed into a field in the search results that are returned to you.uk granny sex chat. Field CTO & Strategic Advisor - Technology & Innovation (m/f/d) splunk combine fields. Field Cto & Strategic Advisor Technology & Innovation (M/F/D), Openings, Vacancies at Splunk in 10115 Berlin Mitte Germany with Skill set Blogs,Data Analytics,Splunk,Communication Skills,Models,Ebooks,Ownership,Legal Requirements,Technology,Consideration,Color,Devops,Cyber Security,It Operations,Leadership,Government,Solution Implementation .. Regional Sales Manager (M/F/D), Openings, Vacancies at Splunk in 10115 .
uk granny sex contact. Additional internal fields are included in the output with the outputcsv command. See Usage . Syntax fields [+|-] <wc-field-list> Required arguments <wc-field-list>. |